Unicast Reverse Path Forwarding
In order for a router to perform its function of forwarding packets it only needs to look at the destination address of the IP packet and never at the source; this allows an attacker to send malformed IP packets using spoofed source IP address and your routers will simply forward these malformed packets to their destinations.
Unicast reverse path forwarding is feature used by network administrators to mitigate the problems caused by address spoofing attacks. When RPF is enabled on an interface, the router examines the source address of each packet it received to make sure it is existing in the routing table with an exit interface matching the interface in which the packet was received on.
If a reverse path does not exist the packet may be dropped (default) or forwarded based on your configuration. If no ACL is configured all packets that fail the check are dropped. If an ACL is configured packets that fail the check will be dropped if matching a deny statement in the ACL else packets are forwarded.
The common use of RPF is to use it on your edge interfaces to ensure that you are not receiving any packets sourced from your addresses coming from outside your network. It also must be configured on routers that have symmetrical reverse paths.
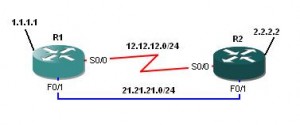
Example:
!-- static routes for loopbacks are configured asymmetrically R1(config)#ip route 2.2.2.2 255.255.255.255 21.21.21.2 R2(config)#ip route 1.1.1.1 255.255.255.255 12.12.12.1
Without URPF configured:
!-- R1 can ping R2's loopback with its loopback as a source R1#ping 2.2.2.2 source lo 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 72/91/120 ms !-- R2 can ping R1's loopback with its loopback as a source R2#ping 1.1.1.1 source lo 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds: Packet sent with a source address of 2.2.2.2 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 64/100/144 ms
Now, lets configure URPF on R1 serial interface:
R1(config)#ip cef R1(config)#int s0/0 R1(config-if)#ip verify unicast reverse-path !-- Ping from R2 to R1's loopback fails because it fails the RPF check (asymmetric routing) R2#ping 1.1.1.1 source lo 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds: Packet sent with a source address of 2.2.2.2 ..... Success rate is 0 percent (0/5)
ACL configuration to allow the ping:
R1(config)#access-list 1 permit 2.2.2.2 log
R1(config)#access-list 1 deny any log
R1(config)#int s0/0
R1(config-if)#ip verify unicast reverse-path 1
!-- lets try the ping again
R2#ping 1.1.1.1 source lo 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 2.2.2.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 96/96/96 ms
!-- This match in the ACL indicates that packets failed in the RPF, but allowed by the ACL
R1(config-if)#do sh access-list
Standard IP access list 1
10 permit 2.2.2.2 log (5 matches)
20 deny any log